Remarkable Women in Maths: Genevieve Grotjan Feinstein
The Woman who Cracked the Japanese ‘Purple’ Code
Genevieve Grotjan Feinstein; Source: NSA
During World War II, both the Germans and the Japanese employed complex cryptography to encode their cables among diplomats and their militaries. The cracking of the Germans’ Enigma code was deemed so groundbreaking that it was portrayed in a popular movie about Alan Turing (who played a key part in decoding it), titled The Imitation Game.
Few people know the story of how US intelligence deciphered the Japanese code called Purple. Yet, the breaking of this cipher proved equally critical to the war effort. Incredibly, the person credited with this breakthrough attended my own alma mater. Meet Genevieve Grotjan Feinstein.
Born in my hometown of Buffalo, New York, Grotjan was the daughter of German immigrants. She joined the University at Buffalo in 1930 as a math major, and even won the William H. Sherk Memorial Prize “for the best paper submitted in any branch of mathematics, pure or applied.”
After spending some time working in Buffalo as a substitute teacher she eventually made her way to Washington DC where, upon scoring very high on a civil service exam, she caught the attention of William F. Friedman. At that time, Friedman ran the research division of the US Army’s Signal Intelligence Service (SIS), the codebreaking organization established in response to the war.
The US National Security Agency (NSA) credits Friedman with “introducing mathematical and scientific methods into cryptology,” by which he solved an earlier version of a German cipher machine in just three and a half hours. Author James R. Chiles said Friedman was “the greatest maker and breaker of secret messages in history — the Harry Houdini of codes and ciphers.” Nonetheless, the Purple cipher would turn out to be an extraordinary challenge.
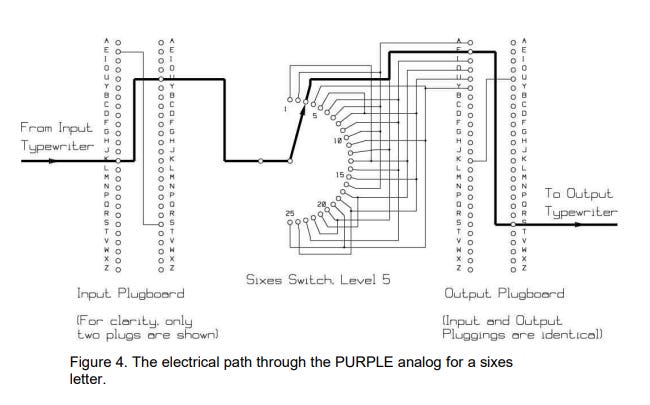
Technically referred to as a “Type B Cipher Machine,” Purple used a substitution cipher with alphabetic letters, converted by a 25-position stepping switch. Upon entering a letter, the device shifted to the next position so that the following letter was encoded entirely differently. A communications officer need only type a message in plain English, and the machine automatically outputted the encoded result.
What made the code more complicated is that the cipher shift depended upon the selected output substitution, meaning that the outputted character could change at any time or every time, rendering the decrypting of a single message unhelpful for determining the meaning of a subsequent message. This process is illustrated here:
Source: PURPLE Revealed: Simulation and Computer-aided Cryptanalysis of Angooki Taipu B
This switching mechanism created a polyalphabetic system with 25 possible solutions for 6 letters of the alphabet, and 15,625 for each of the remainder. The physical structure of the machine, however, contained the critical flaw that would later lead to breaking the code. Electrical contacts were connected to a rotor, but were split into groups of 20 and 6. This setup mirrored the construction of a previous machine called Red, which American cryptographers already understood.
With this knowledge in hand, solving the 6 letters turned out to be simple, as each had only 25 possibilities. This left them with the problem of resolving the remaining 20 letters—no small feat. The number of possibilities for the remaining 20 letters allowed virtually every subsequent message to invoke an entirely new permutation of the cipher.
Grotjan and the cryptoanalysis team began working on the remaining code by employing frequency analysis. Put simply, cryptographers merely count the number of times a specific letter appears in encrypted messages. In most languages, certain letters (such as vowels) and combinations of letters (such as ss or ll) appear at consistent rates.
By analyzing the number of times and locations these letters or combinations show up in a message of sufficient length, codebreakers can make educated guesses about portions of various words. Shorter messages render this method ineffective because there is not enough data to make assumptions. Other practices also complicate or reduce the efficacy of this method, such as using abbreviations or misspelling words.
In the case of Purple, codebreakers also had to deal with proprietary shortcuts or unconventional transliterations of words. As an example, Japanese communications personnel used the letter L in place of ai wherever that combination occurred. Moreover, they used 3-letter combinations to represent punctuation, such as CFC in place of period dots.
Here is an example of frequency analysis. Letters are assigned numerical values to represent their tendency to appear in the text. These numbers can then be run to determine the mathematical value of their combination potentially equaling a specific word. Source: Mekhaznia Tahar
Finally solving the code became possible when Grotjan discovered a reproducible pattern in the ciphered text. Other cryptologists had been working on it for months prior to her joining the team. Her discovery proved so important that her supervisor, Frank Rowlett, exclaimed “That’s it! That’s it! Gene has found what we’ve been looking for!”
Friedman later described her breakthrough as “the most important source of strategically valuable, long-term intelligence” in the war. While the newly revealed Purple code did indeed provide valued intelligence, the Japanese did not use it for coordinating its attack on Pearl Harbor, so Purple’s discovery could not prevent it. Nonetheless, it remains a remarkable achievement in the history of codebreaking.
After defeating Purple, Grotjan continued to impress. She next contributed to deciphering the Venona messages, the codename for encryption used during and after the war by the Soviet spy agency known as the KGB (Комитет государственной безопасности (КГБ)).
Used by both Soviet diplomats and spies, unmasking the Venona messages provided an abundance of actionable intelligence all the way up until 1980. Perhaps the biggest revelation from that trove was the treasonous activities of Julius and Ethel Rosenberg. Infamous among American anti-espionage personnel, the Rosenbergs were convicted of and executed for conspiring to pass US atomic secrets to the Soviets in 1953.
The US President at the time, Dwight D. Eisenhower, stated “I can only say that, by immeasurably increasing the chances of atomic war, the Rosenbergs may have condemned to death tens of millions of innocent people all over the world. The execution of two human beings is a grave matter. But even graver is the thought of the millions of dead whose deaths may be directly attributable to what these spies have done.”
Grotjan added her husband’s surname, Feinstein, when she married Manhattan Project chemist Hyman Feinstein in 1943. The couple had one son who died tragically at the age of 22. In 1946, Grotjan received the Exceptional Civilian Service Award from Brigadier General Paul Everton Peabody for her cryptography efforts.
In 1947, she left government service to teach math at George Mason University. Her husband died in 1995, but not before establishing the Genevieve Feinstein Award in Cryptography at George Mason University. Grotjan died in 2006, at age 93. In 2010, the NSA posthumously inducted her into its Hall of Honor. Hers is a story of yet another woman’s amazing achievements, unfortunately buried in the annals of history. I am happy to have had the opportunity to retell her story. Thanks for reading.
Grotjan and her husband, Hyman Feinstein (above), enjoyed dinners with neighbors and friends in Fairfax, Virginia. Photo courtesy of Joan Craun; Source: University at Buffalo
* * *
I am the executive director of the EALS Global Foundation. If you like my work, you can also follow me at the Evidence Files Medium page for an exploration of law, politics, history, and social issues; or Buy me a Coffee as a small show of support.