Cookies
A web or browser cookie is a form of communication that a Web server sends to a Web browser. There are two primary types: Session and Persistent (Permanent) cookies. The difference between them is how they are stored and how long they exist. Session cookies are stored in temporary memory and have a lifespan that depends upon the parameters of the browser. Session cookies last as long as their name suggests—for the duration of the user’s session. Unfortunately, this is a bit misleading because some browsers use a “session restore” function, which automatically restarts the user’s previous session thereby giving indefinite life to the associated cookies. Persistent cookies, sometimes called Permanent cookies, tend to have an expiration date determined by the Max-Age attribute. Chrome developers, for example, can set the maximum age to no more than 400 days, but the Max-Age limitation varies by browser. These cookies are stored in the device memory.
Cookies generally perform any of three basic functions:
Session management - Logins, shopping carts, game scores, or anything else the server should remember
Personalization - User preferences, themes, and other settings
Tracking - Recording and analyzing user behavior
We discuss these in more detail below, but the first two functions are largely designed to enhance the user experience. Cookies enable the website to immediately configure to known user preferences (information stored in the cookie and conveyed to the web server). They also let the website “remember” important pieces of user-provided information, such as what items the user put in a cart or where the user left off in an online game. Tracking cookies provide information about the user’s activities or behaviors to the web server for uses such as marketing.
The Pros and Cons of Cookies
When a user seeks to “go” to a website, their browser sends an HTTP request. This is called a “client-server” protocol where the user (the client) makes the request and the web server “responds.” Servers tend to respond, in part, by including one or more Set-Cookie headers. These headers provide a name and value for each cookie, and direct the client to store them. For future interactions with the same server, the client-browser will send the relevant cookies along with each request. By that method, the web server immediately recognizes a returning user and can therefore apply the various settings or other memory items mentioned above. Most cookies on commercial sites now use the Secure attribute employing encrypted requests making them more secure.
The pros of cookies are obvious. Without cookies, every time you visited a new link on a site your shopping cart would be reset to zero, which might make online shopping difficult or annoying! Cookies also allow users to store login information, review things they downloaded from the site, or simply return to places browsed previously. Before we discuss more complicated aspects of cookies, there are some standard drawbacks. Cookies are files, and files take up space, so an overabundance of stored cookies can inhibit performance. While very small, because session cookies can last virtually forever, a user can collect extraordinary amounts of them. In addition, cookies essentially feed the web server information, so under certain conditions this can slow the performance of the web page as it ingests all of the cookies’ information. On the flip side, deleting cookies might also slow the website experience because the user will have to re-enter any needed information. Disabling cookies altogether might also prevent the user from accessing certain features of a website.
The more nefarious aspects of cookies
Cookies have a positive purpose—enhancing the user’s web experience. As with most technology, however, some people employ them for nefarious designs. Probably the most frequent undesired use of cookies is for tracking users. Sophisticated systems can link a user’s recorded activity to their real identity even if the cookies themselves do not directly reveal a user or their device info. All cookies can enable tracking of a user to various extents. Third party cookies—those belonging to a domain different from the one the user intends to visit—typically comprise those most often employed in the more sinister forms of user tracking. In almost all cases, the data collected is sold for advertising purposes.
Third party cookies enable the tracker to collect information about the user every time a user visits a website that employs a resource owned or controlled by the tracker. The definition of a resource is rather nebulous, but can include any aspect of interaction with a page—even the analytics of visitor traffic. This means that a user can receive third-party cookies often without doing anything more than visiting a site. As an example, while browsing a retail website, the user receives a tracking cookie from the site that contains a unique ID to identify the user’s browser. When visiting a different site that recognizes that ID of the tracking cookie, it displays an ad based on what the user did on the previous site. Big companies like Google and Facebook sell this service to smaller websites. When users visit these smaller sites, they see advertising based on their (much more prolific) use of those bigger sites. The owner of the tracking cookie continues collecting this information as long as it resides on the machine or in the browser, accumulating it to the point that an extraordinary profile can be created—and sold—delineating all the habits of a user’s online activity.
Supercookies
Regular cookies can be both wonderful and invasive. Yet, the user generally can control the amount of them present on their device. Almost all browsers contain cookie removal options in the settings, and antivirus programs are pretty good at detecting and removing those that appear potentially malicious. Supercookies enable tracking, but in a way that is virtually impossible to detect or prevent. Internet Service Providers (ISPs) create cookies that store information about the user’s device, browser, and browsing information. Unlike other cookies, however, these are stored on the ISP’s servers and contain Unique Identifier Headers (UIDH) that recognize specific devices and what they are doing online. Individual browsers contain a lot more information than people realize. To see it firsthand, test yours at the Electronic Frontier Foundation’s Browser Fingerprint Tool.
The ISP tracks what the user does online by inserting information into the data packets transmitted between the internet and the identified user/device. As these supercookies never actually touch the user’s device, there is no way to delete them and no legal way to access them. A user’s only option is to stop them from tracking in the first place. Probably the simplest way to prevent this kind of ISP spying is to employ a Virtual Private Network (VPN). Because traffic routes to the VPN server first before rerouting to the internet, the ISPs spying ability ends there. It cannot track the user beyond the VPN server. There are drawbacks to using VPNs, however. See this article for more details.
Saturday Shorts: VPNs
A Virtual Private Network (VPN) is basically a piece of software that tunnels your internet traffic from your device to a VPN server, then out to the internet. VPNs encrypt your data and prevent your Internet Service Provider [ISP] (and others) both from reading that data and from seeing where it goes onto the internet. The only thing the ISP knows is t…
Examining the Cookies on your machine
There are several ways to view, analyze, and manipulate the cookies stored on a user’s machine or browser. We discuss just two of them here, but begin with the caveat that for the average user, manipulating cookies without sufficient knowledge might severely affect subsequent online activity. The methods described here are for educational purposes only; neither Bishal nor I recommend performing any actions without assistance or proper knowledge.
We say again: Warning!! Manually fiddling with cookies can have unforeseen circumstances.
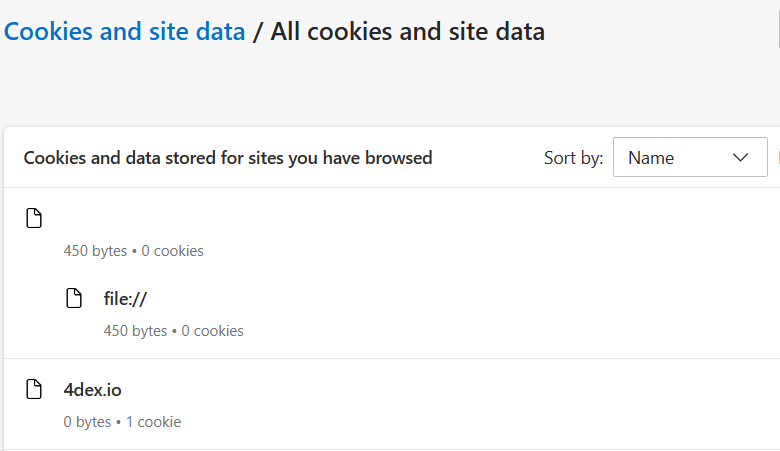
Method 1: View all the saved cookies in the browser settings. Typically, to access these menus go to the browser settings —> site permissions / privacy / security —> cookies and site data (will vary slightly across different browsers). In the Microsoft Edge browser, it looks like this:
It is safe to simply view cookies through this method, so long as no further action is taken. We recommend having a look, however, because most users will be somewhat awed by the sheer number of cookies residing within their system. It is possible to delete cookies from this screen, so be careful not to click on the garbage can icon or other delete buttons. The benefit here is to see how much space the cookies consume in total and to see what sites implanted them (though in some cases it is difficult or impossible to tell).
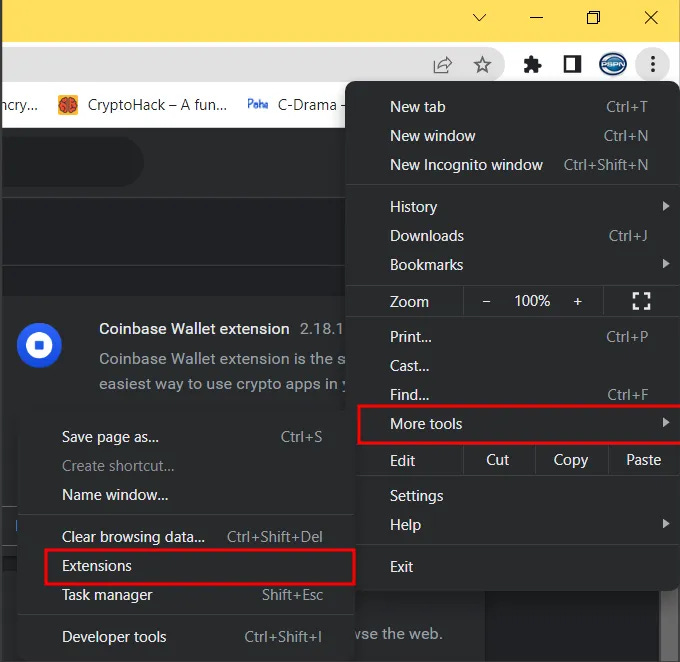
Method 2: Install the cookie-editor extension for your preferred browser. Browser Extensions are essentially nothing more than pieces of software that add some functionality to an existing browser. The images below depict the cookie-editor extension as used in the Chrome browser. Click on add to Chrome to get started.
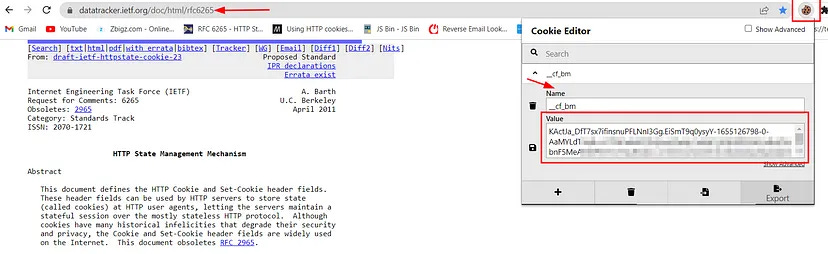
Go to extensions and turn on the cookie-editor to see the assigned cookies of websites you visit. The example below shows the results after visiting the website datatracker.ietf.org:
Tools like this provide much more detailed information and are especially useful for analyzing troublesome or malicious cookies. Other open-source tools exist to engage in deeper analysis, such as deciphering the value codes of a specific cookie (as indicated in the red box in the image). In many cases, the origin, purpose, and other information from the cookie’s value can be found with various tools or even through online searches.
We advise proceeding with caution working with cookies. Deleting them might cause you to lose login or password information or could simply cause a big headache when accessing sites you regularly visit. Moreover, some sites will not work correctly—or at all—without certain cookies. In other cases, engaging (in a way beyond mere viewing) a malicious cookie might provide the spark needed for it to run a malicious command or perform some other insidious activity. There are some cookies, however, you might wish to remove. Examples of those you might consider removing are unwanted Third Party cookies, those from unencrypted websites, cookies from sites you no longer visit or visit very infrequently, cookies your antivirus software identifies as suspicious, or those generated when filling in personally identifying information (PII). How to do so depends upon the browser you use, but most provide detailed instructions online. For the uninitiated, the safest method is to use the available browser tools to remove them, not to try to do so manually, one-by-one.
Other online tools provide various methods for viewing and analyzing cookies. In every instance of using an open-source tool, the user must take precautions about what data is provided and what level of access to the system the user allows. Nonetheless, tracking the cookies stored on a device or in one’s browser is one method toward controlling privacy and monitoring performance.
***
I would like to thank my special guest author Bishal Aryal. Mr. Aryal is a Security Engineer at TechKraft, Inc. and a student of Coventry University through Softwarica College of IT & E-Commerce in Nepal. This article built off of a previous one published on Mr. Aryal’s Medium page available here.
I am a Certified Forensic Computer Examiner, Certified Crime Analyst, Certified Fraud Examiner, and Certified Financial Crimes Investigator with a Juris Doctor and a master’s degree in history. I spent 10 years working in the New York State Division of Criminal Justice as Senior Analyst and Investigator. Today, I teach Cybersecurity, Ethical Hacking, and Digital Forensics at Softwarica College of IT and E-Commerce in Nepal. In addition, I offer training on Financial Crime Prevention and Investigation. I was a firefighter before I joined law enforcement and now I currently run a non-profit that uses mobile applications and other technologies to create Early Alert Systems for natural disasters for people living in remote or poor areas.
Find more about me on Instagram, Facebook, Twitter, LinkedIn, or Mastodon. Or visit my EALS Global Foundation’s webpage page here.
Visit the new Evidence Files Facebook and YouTube pages; Like, Follow, Subscribe or Share!
For another article on protecting your digital activity, see here.
How Strong are your Passwords?
In today’s world we all have so many passwords. Banking, social media, email, online retailers, employment… so, so many. It is hard to keep track of them all. Yet, the password remains the primary point of security for a great many things we wish to protect. Heck, there is even a thing called the