Visit the Evidence Files Facebook and YouTube pages; Like, Follow, Subscribe or Share!
In today’s world we all have so many passwords. Banking, social media, email, online retailers, employment… so, so many. It is hard to keep track of them all. Yet, the password remains the primary point of security for a great many things we wish to protect. Heck, there is even a thing called World Password Day (the first Thursday in May). This seemingly ridiculous-sounding day of observance is to encourage people to change their current passwords, add two-factor authentication (2FA) or take certain other internet-related precautions. Among all the people of the world using dozens of password-protected accounts each, there are billions of passwords floating around, and a lot of them are terrible. Are yours?
Unfortunately, people are not good at remembering long, complex character strings that infosec officials keep telling them to adopt. Secureframe reports that at least 65% of people use the same password for at least two accounts, 33% use easy-to-remember passwords, 36% do not believe they will ever be targeted and thus employ bad password habits, and 15% of users even have their first name as part of their password. The problem is that bad password habits lead to breaches all the time. Sometimes these breaches target individuals, sometimes companies. Company breaches are especially pernicious because a single employee utilizing a weak password can provide the attacker a vector to enter company systems and steal everyone else’s credentials, no matter how solid the rest of them might be.
So, what’s in a password?
Most platforms now store passwords as hash values. Hashes essentially work like a cipher, using a mathematical formula to scramble the text (and other characters like numbers or !, @, #, etc.). Hashed passwords cannot be resolved in the reverse. A standard password meeting the usual requirements of upper and lower case letters, numbers, and special characters might look like: Dr23@@aq1a11c)(x. The resulting MD5 hash of that password comes out as: 079CA1D94BD0E41B61C2B3F46EFC9AF6. [Note that there are a variety of hash types, SHA1, SHA 256, SHA512, Blake3, etc., but MD5 remains the most common form used for password security]. Because hackers cannot resolve hashes in the reverse, they enter them into programs to “crack” them. In plain terms, they use software to attempt every possible combination of letters, numbers, and special characters, hash them, then run the hash results against stolen hash value databases for hits. When they find one, they know they possess a viable password. As computing power increases, the numbers of possible combinations a hacker can attempt per second also increases… enormously.
In the “old days” (like 3-4 years ago), hackers ran these computations with a computer’s Central Processing Unit (CPU). CPUs run processes in order, one after the other. Generally speaking, the main feature that determined calculation speeds for CPUs was the number of cores available. So, for instance, a CPU with 64 cores can calculate far faster than one with just 32. Now, most password breakers run calculations with the Graphics Processing Unit (GPU). The GPU subdivides processes into numerous smaller operations and conducts them simultaneously, enabling far faster computation times. The two—CPU and GPU—can also work in tandem, creating potentially exponentially faster computation capability.
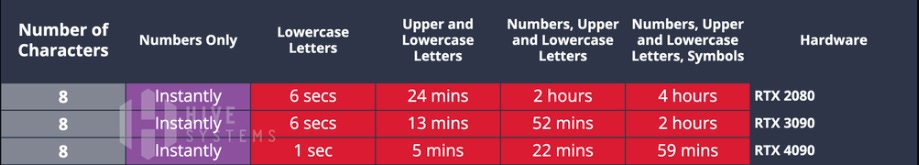
When an attacker decides to target an individual’s password, he or she puts that computing power to work. While I won’t get into the ways people steal hash values, history makes it clear that this happens all the time and there are a variety of ways to do it. When targeting an individual, attackers often have contextual information (such as an email address, phone number, or username list) to consult in conjunction with the password once they acquire it. Sadly, even careful users cannot keep much of this very useful information from public, prying eyes. How fast, then, can all this computing power ascertain a user’s password? In 2018, using the RTX 2080 graphics card (GPU method), researchers calculated 37.085 billion hashes per second. In 2020 with the RTX 3090 card, 70 billion per second, and in 2022 with the RTX 4090, 164 billion per second. For an 8-character password, this resulted in times as indicated here:
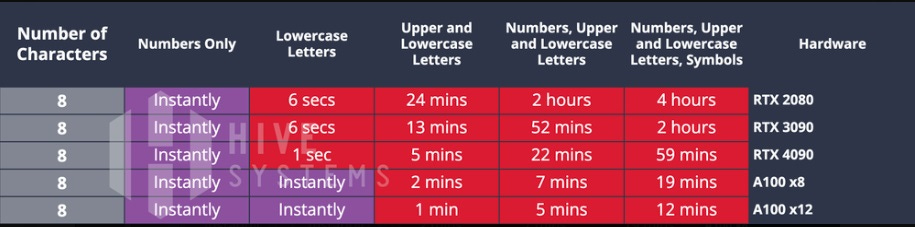
From 2018 to 2022, cracking time reduced by three hours adopting just a single GPU available publicly. It gets worse. Hackers now can employ cloud computing, which essentially adds free GPUs to their calculation matrix. These GPUs are available to anyone because they are intended for use on legal things. Nevertheless, when employed in criminal activity, here is the result. Note that the bottom lines indicate the time it takes calculating with two Amazon cloud services, one of which includes 8 cloud GPUs and the other with 12 GPUs.
The 8-character password with the most complexity went from a cracking time of one hour to just 12 minutes. And it gets worse, still.
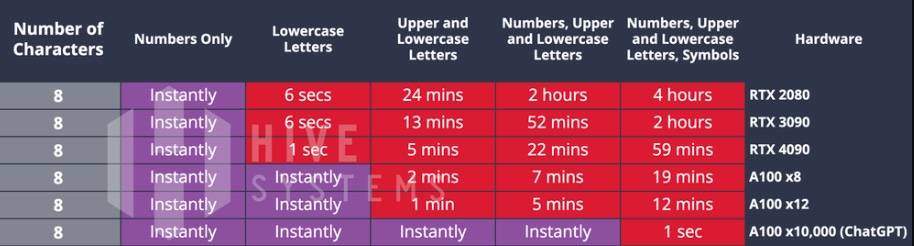
Hackers now have the option to recruit artificial intelligence for computing assistance. Microsoft Azure offers services employing 10,000 GPUs. Hive Systems, the researchers whose work I relied on for the calculation times and tables in this article, determined how employing ChatGPT (running 10,000 GPUs) affects password breaking time:
As you can see, even the most complex 8-character password is no match. Integrating ChatGPT into the cracking program led to a maximum time of 1 single second to crack any 8-character password. So, how strong does your password need to be if employing MD5 hashing as its protection?
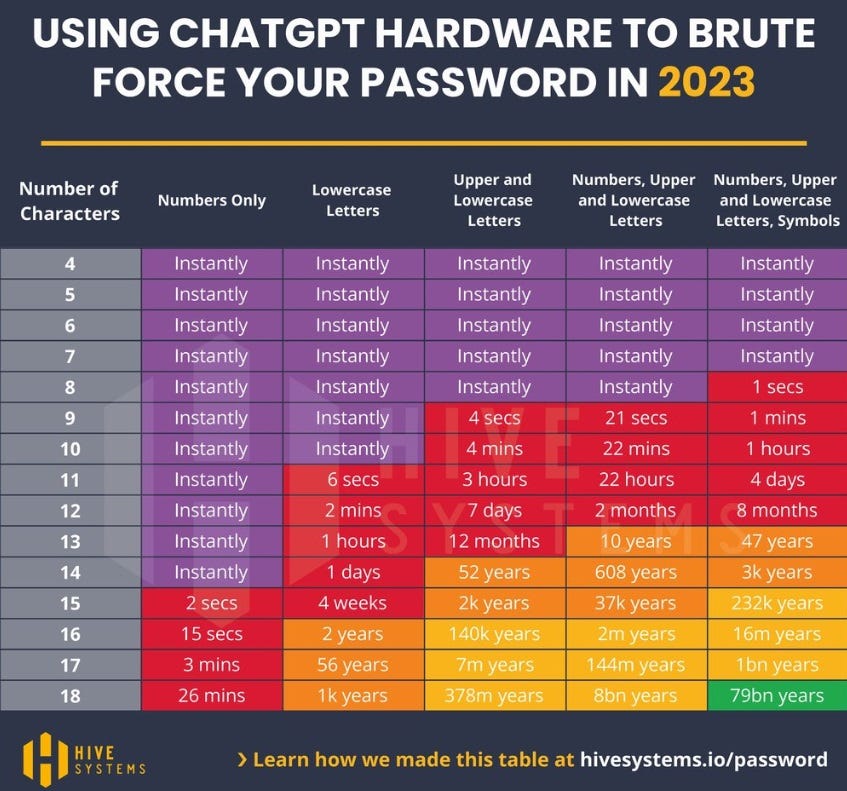
Not good news for weak, or even modest, password users. Hackers can crack an 11-character password in 4 days or less. And remember, the times listed here are the maximum it would take to run every possibility. Most likely, it will require far less time.
What to do.
Importantly, the user has no control over the hash algorithm a particular platform uses to encode passwords. One should assume it will be MD5, as this remains the most common. Therefore, the last table above is the metric by which to measure how long and complex a password should be. The difference between the cracking time of a 12- versus 13-character password suggests one should always use at least 13 characters, including all the specialties (capital and lower-case letters, numbers, and symbols). Passwords should never have regular words within them. Incorporated in most cracking programs is what we call a dictionary attack. Passwords with dictionary words found within them greatly decrease calculation times for cracking and thus are far more vulnerable. The same goes for common names.
You should not use personal information within your password, like date or year of birth. If a hacker targets you specifically, chances are s/he knows that information from internet searches and can incorporate it into the cracking strategy. Use random character threads. Repeating keys to make it easier to remember also makes it easier to break. Computer programs love patterns! Never reuse passwords. This includes both using older ones again later or using the same one for more than one platform. If a password is ever stolen, the hash is out there for hackers to find. When hackers target an individual, they will first run that hash against lists of known hash values for which the password has already been cracked. Using such a password can be discovered in fractions of a second. Don’t think you are too unimportant to be targeted individually. Most data breaches of major companies start with the individual. You may think as a low-level employee, your inferior status will prevent anyone from targeting you. Alas, not necessarily so. Your permissions on a company network might be all the hacker needs for the attack plan. You will never know until it is far too late. Finally, use extreme caution in where you enter your password. Phishing and spear-phishing are among the most common infiltration methods that lead to large breaches. For more on how that works, read the article below on how attackers target you through email.
Two-factor authentication, password managers, biometrics and other methods can be used to enhance personal security. Right now, though, the strength of your password remains a critical defense. Follow the steps above to keep yours as safe as possible while infosec researchers work to develop the next best thing.
***
I am a Certified Forensic Computer Examiner, Certified Crime Analyst, Certified Fraud Examiner, and Certified Financial Crimes Investigator with a Juris Doctor and a Master’s degree in history. I spent 10 years working in the New York State Division of Criminal Justice as Senior Analyst and Investigator. Today, I teach Cybersecurity, Ethical Hacking, and Digital Forensics at Softwarica College of IT and E-Commerce in Nepal. In addition, I offer training on Financial Crime Prevention and Investigation. I am also Vice President of Digi Technology in Nepal, for which I have also created its sister company in the USA, Digi Technology America, LLC. We provide technology solutions for businesses or individuals, including cybersecurity, all across the globe. I was a firefighter before I joined law enforcement and now I currently run a non-profit that uses mobile applications and other technologies to create Early Alert Systems for natural disasters for people living in remote or poor areas.
Find more about me on Instagram, Facebook, LinkedIn, or Mastodon. Or visit my EALS Global Foundation’s webpage page here.






Thank you.. this was the best advice in today's world people need as tech hacks are out to get us at every corner..