Visit the Evidence Files Facebook and YouTube pages; Like, Follow, Subscribe or Share!
The term honeypot enjoys a history dating back about a century, defined as “one that is attractive or desirable,” More broadly, it represents “a place, thing or person that a lot of people are attracted to.” In the world of espionage, a honeypot is “an operational practice in which a covert agent utilises a romantic or sexual relationship to compromise a target for valuable intelligence.” In cybersecurity, we have them too—not the sexual relationships (typically), just the places to which an attacker is attracted.
A honeypot is a commonly employed tool by cybersecurity specialists to defend against cyber attackers (i.e., hackers). It is essentially a decoy, dressed up like a real network or machine, but laden with one or more vulnerabilities meant to attract ne’er-do-wells. Designers of honeypots might insert an unencrypted database (of fabricated information) or leave open ports that respond to port scanners. The purpose is not to address a particular problem; rather to identify and analyze those who attempt to exploit whatever weakness(es) the designers provided to bolster security measures, all done within a secure environment.
Some honeypots use automated systems to detect, flag, and block potentially malicious software. Email traps, for example, reside in an area where only an address harvester would detect them. Incoming messages to the given address would almost certainly constitute spam, so cybersecurity teams can set the system to automatically block repeat offenders. Spider honeypots employ a similar tactic against webcrawlers, allowing for automated blocking of malicious bots or automated adware injections.
Low-interaction honeypots simulate little more than a basic machine. The name suggests their capability—attackers cannot do much, and relatively little information is collected on them. Nepenthes, named for the Venus Fly Trap, contained a default set of vulnerabilities deployed in a production network. When exploited, Nepenthes’ detectors would send an immediate alert to system administrators allowing for a rapid response. Moreover, this program did enable the collection of certain data, including:
MD5 values of the malware samples
Malware Binaries
Pcap data & network traces
Analysis results including antivirus labels etc.
IP address information
Logs of the downloaded, submitted binaries
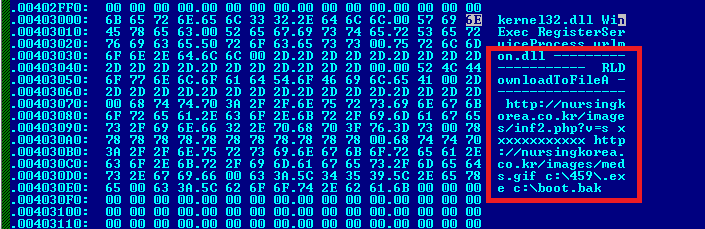
This limited dataset contains important information. MD5 values are hashes of the malware sample, which enables easier autodetection of future attacks using the same malicious software. Malware Binaries are basically just the size, and sometimes the configuration, of the infectious code. Pcap data means captured data packets. Data packets captured from network traffic comprise the content and instructions of specific pieces of information sent to or received from a network. This data allows examiners to determine what each piece of data is, and what it is meant to do. A network trace is like listening to the entire conversation between the client (user) and server. This adds helpful context to Pcap data. Antivirus labels might also be called “signatures,” which are “a continuous sequence of bytes that is common for a certain malware sample.” Malware downloaded from the internet for use by attackers frequently contains such signatures.
Example in red constitutes the signature code. Source: Kaspersky Labs
The value of IP address information is obvious to cybersecurity folks. For the rest, the IP address acts like a footprint in the snow near a crime scene. By itself, it tells us quite limited information. But, it might indicate the criminal’s shoe size, type of shoe, direction of travel, etc. IP addresses provide threat researchers the same type of information in a cyber context. Submitted binaries refers to code which is not compiled, meaning the researcher will have limited pieces of a malicious program to analyze because the code is executed remotely, rendering only resident pieces (or none) of it available to the examiner.
High-interaction honeypots provide attackers real operating systems or applications in which they can play. Here, the attacker can engage in much more activity, providing a great deal more information to analysts. A carefully crafted honeypot of this kind might allow analysts to effectively surveil an attacker in real-time, especially in the instances where the attacker does not figure out the ruse. One month ago, Techcrunch reported that two researchers deployed an extremely sophisticated honeypot comprised of several Windows servers utilizing RDP (Remote Desktop Protocol). Throughout 100 hours of surveillance, the researchers recorded 190 million events in which the attackers engaged. These events included:
[I]nstalling malware that mines cryptocurrencies, using Android emulators to conduct click fraud, brute-forcing passwords for other computers, hiding the hackers’ identities by using the honeypot as a starting point for another attack, and even watching porn.
The hackers assumed various roles; some conducted reconnaissance of the network’s security, changing passwords, brute-forcing into other computers, and hiding their activities. Others, apparently the lower-skilled or less motivated, used their access simply to download pornography that was banned in the country in which they operated. Note that the drawback of these kinds of honeypots is that they create a vector of vulnerability for more sophisticated attackers because they open the door to the infiltration of real networks.
The primary benefit of honeypots is to detect malicious activity that otherwise would be directed toward tangible, and important, assets like a company’s actual network. It helps identify such activity in a (relatively) safe, controlled environment, which allows time for analysis and defense planning before the attacker directs his or her resources toward the target of actual value. Nonetheless, employing honeypots requires resources—both technical and human. On the technical side, the more sophisticated the honeypot, the more server space and technical tools will be needed. Without humans to monitor and respond to what happens within the honeypot, its efficacy will be limited to automated programs, such as in the case of email traps and spider honeypots.
There also remain some questions—depending upon the jurisdiction—of the legality of honeypots. Allison Grace Johansen, writing for Norton, notes that “the questions of whether honeypots are illegal and unethical is worth considering.” She queries whether a honeypot enticing someone who is not a hacker might lead to privacy violations (particularly under the stringent General Data Protection Regulation of the EU). This is a good, if very fuzzy question. Moreover, she ponders whether a honeypot might lead to legal entrapment of infiltrators. Entrapment means that law enforcement “induc[es] the defendant to engage in a criminal act that the defendant would not otherwise have committed.” Frankly, I think Johansen is far off on this one. Cybersecurity people who are not acting under the direction of law enforcement are not bound by this provision—thereby abrogating it as the affirmative defense that it normally is. Moreover, simply creating vulnerabilities does not—to me at least—seem to “induce” someone to exploit them. Finally, she cautions against the live surveillance element of high-interaction honeypots, noting it might run afoul of the US Federal Wiretap Act. I’ve had this very debate (sometimes heated) with other law enforcement agents.
On this last issue, what Johansen is referring to is 18 U.S. Code Chapter 119, the Wire and Electronic Communications Interception and Interception of Oral Communications law. In § 2511, it prohibits anyone who
Intentionally intercepts, endeavors to intercept, or procures any other person to intercept or endeavor to intercept, any wire, oral, or electronic communication.
But § 2511(2)(a) seemingly provides the exception:
It shall not be unlawful under this chapter for an operator of a switchboard, or an officer, employee, or agent of a provider of wire or electronic communication service, whose facilities are used in the transmission of a wire or electronic communication, to intercept, disclose, or use that communication in the normal course of his employment while engaged in any activity which is a necessary incident to the rendition of his service or to the protection of the rights or property of the provider of that service, except that a provider of wire communication service to the public shall not utilize service observing or random monitoring except for mechanical or service quality control checks.
[My] bolded section seems to curtail any concern about unlawful uses of honeypots for the purposes of protecting a network or data from external attack, even if the methodology involves live surveillance. Unsurprisingly, very few court cases discuss the issue, and none discuss the merits of a honeypot’s application. In any case, anyone intending to deploy a honeypot should check with legal authorities or experts.
For now, honeypots continue to assist cyber researchers in identifying malicious activities and potentially malicious software. Their construction remains a work as much of art as science, requiring cybersecurity professionals to “think like a criminal” to enhance their efficacy. This article was meant as a primer for those who wish to explore the topic more thoroughly.
***
I am a Certified Forensic Computer Examiner, Certified Crime Analyst, Certified Fraud Examiner, and Certified Financial Crimes Investigator with a Juris Doctor and a Master’s degree in history. I spent 10 years working in the New York State Division of Criminal Justice as Senior Analyst and Investigator. Today, I teach Cybersecurity, Ethical Hacking, and Digital Forensics at Softwarica College of IT and E-Commerce in Nepal. In addition, I offer training on Financial Crime Prevention and Investigation. I was a firefighter before I joined law enforcement and now I currently run a non-profit that uses mobile applications and other technologies to create Early Alert Systems for natural disasters for people living in remote or poor areas.
Find more about me on Instagram, Facebook, Twitter, LinkedIn, or Mastodon. Or visit my EALS Global Foundation’s webpage page here.
For more on exploring malware, check out below. Thanks for reading!